Pain and Suffering: Climbing the Pyramid of Pain
Pain and suffering is the last thing you wish happen to you. This goes to information security as well. As a security professional who are in the domain of threat intelligence often face cyberthreat on daily basis. Given these challenges, security professionals have to stay ahead in detecting, preventing, and mitigating threats to defend their organizations.
In this blog post, we will uncover "Pyramid of Pain", a cyber defense frameworks that will help security professionals to help with threat detection and mitigation.
💡 Learning Advice: Whenever you want to learn any frameworks, it is important to know what is the framework, for whom the framework is designed, what is the need for the framework to exist, and how the framework contribute in the industry.
What is "Pyramid of Pain"?
Defining the concept of the framework.
Pyramid of Pain is an information security framework that emphasize in defending the security posture of IT infrastrure within an organization. The framework is designed by DavidJBianco in 2013. The term pyramid is choosen due to the framework is illustrated in the shape of pyramid. It symbolizes IOCs from the less painful to most painful - from bottom to the top level. An Indicator of Compromise (IoC) is a piece of evidence or artifact that suggests a security breach or cyber attack may have occurred.
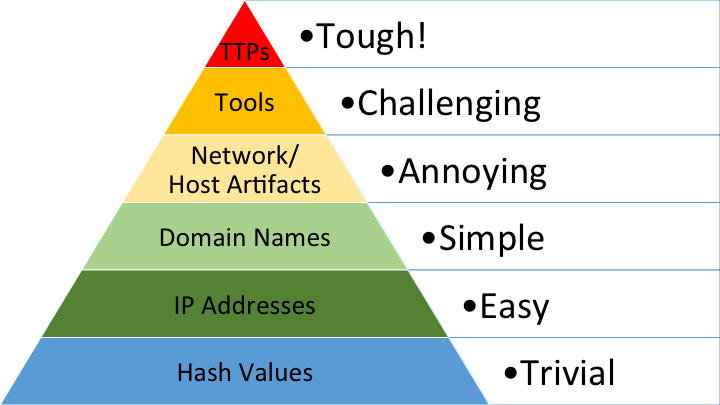
Image below illustrates "Pyramid of Pain".
As seen in the image above, there are six levels of Indicator of Compromise (IOC). The six levels of IOCs in the Pyramid of Pain are arranged in a way how "painful" it would be for the attacker if the victim detected them and took action against them. Those six levels of IOCs are listed and explained below:
Hash Values (Trivial): A hash value is a piece of cryptographic output that derives by inputting a file. The output is uniquely assigned to a file which we call it as a file signature. No two files should have the same cryptographic hashes.
IP Addresses (Easy): Internet Protocol (IP) Addresses are the symbolisation of a device connected to the Internet. There are no scenarios where a device can be connected to the Internet without an IP address assigned to it.
Domain Names (Simple): Domain name is a string of text that used to identify a resource available on Internet such as website and server.
Network/Host Artifacts (Annoying): A network artifact is a product of network activity, while a host artifact is a product of host activity on a host endpoint.
Tools (Challenging): Tools are used by attackers to carry out scanning or exploitation such as scripts and backdoors.
TTPs (Tough): Tactics, Techniques, and Procedures (TTPs) is a modus operandi that identify attackers. It consists from the initial method of entry, all the way to laterally moving across the victim's network and exfiltrating data.
Who is this framework for?
Highlighting who should use this framework to better the security posture.
"Pyramid of Pain" is undeniably a valuable conceptual model that can be referred by security professionals. Though this framework often utilised by security analyst and security architect, the framework itself is not restrictive to any particular domain within information security. It is possible for both red and blue team people to make use of this framework.
Red Team
Red teams can use the Pyramid of Pain as a guide for developing and executing their penetration testing or adversary simulation campaigns. By focusing on the higher levels of the pyramid, red teams can test an organization's ability to detect and respond to advanced threats and attacks.
For example, if a red team is able to successfully use a low-level IOC, such as a hash value or an IP address, to gain access to an organization's network, it may not be a good indicator of the organization's security posture. However, if the red team is able to use a higher-level IOC, such as a specific domain name or a unique file name, it is a stronger indicator that the organization has weaknesses in their security defenses.
Moreover, the red team can use the Pyramid of Pain to identify the most effective tactics, techniques, and procedures (TTPs) to use during their engagement. By using the higher-level IOCs, the red team can identify which TTPs are most effective in evading detection and response.
Blue Team
Blue teams can focus their efforts on identifying and monitoring the higher-level IOCs, which are more difficult to detect and respond to. For example, if a blue team identifies a specific domain name or file name associated with a threat actor, they can use that information to hunt for other related indicators, such as IP addresses or command-and-control (C2) servers, which may be less obvious and more difficult to detect.
By understanding the difficulty level of various IOCs, blue teams can also better assess the effectiveness of their defensive measures. For example, if a blue team has deployed a security solution that is able to detect low-level IOCs such as IP addresses, but is ineffective against higher-level IOCs such as specific domain names or file names, they can use that information to improve their defenses and prioritize the deployment of more effective security controls.
Why this framework need to exist?
Explaining the existence of this framework even there were many framework serve the same purpose.
Indeed there are many other frameworks in existence, each framework may have its own unique perspective or methodology for identifying and prioritizing IOCs based on various factors such as the difficulty of detection, the level of sophistication of the attacker, or the potential impact of the attack.
One reason why the Pyramid of Pain has gained popularity is its simplicity and intuitive nature. It provides a clear visual hierarchy of IOC difficulty that can be easily understood and communicated to stakeholders across an organization. This framework has also been embraced by the cybersecurity community, and many security vendors and organizations have adopted it as a way to prioritize and categorize IOCs in their products and services.
How this framework contributes to the industry?
Each framework should contribute a purpose to the industry.
The Pyramid of Pain framework can contribute significantly to the information security industry by providing a standardized approach to the classification and prioritization of indicators of compromise (IOCs). By understanding the difficulty level of different IOCs, organizations can prioritize their defense efforts and allocate their resources more effectively to protect against advanced threats.
Additionally, the Pyramid of Pain can guide incident response efforts by helping security teams to determine the level of sophistication of the attacker and the potential impact of the attack.